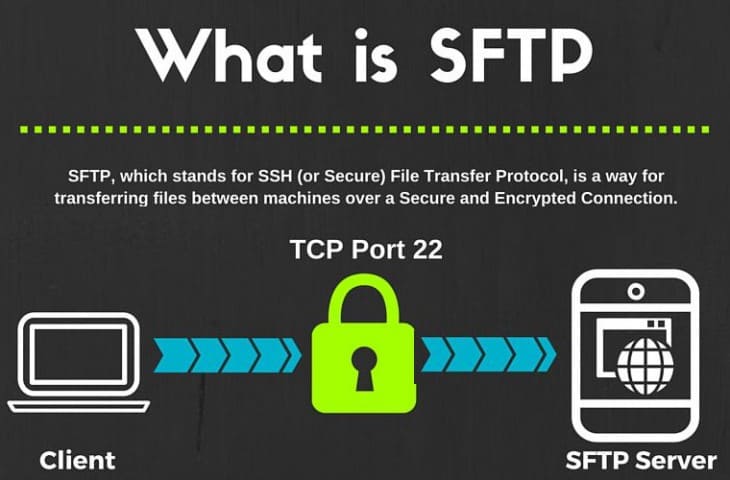
Recently, Microsoft has released a port of OpenSSH for Windows. You can use the package to set up an SFTP/SSH server on Windows.
The SSH File Transfer Protocol is a network protocol that provides file access, file transfer, and file management functionalities over SSH. By using SFTP, you can easily change, browse, and edit files on your Raspberry Pi. SFTP is easier to set up than FTP once Raspberry Pi OS has SSH enabled. For security reasons, since the November 2016. Protect the private key with a passphrase. Keep the passphrase and private key file secret, only share the public key with us. Send the public key to our support live chat on our website or email to support@hostifi.com, and request access to the unifi user on your server for SSH/SFTP. We will install it and write you back when done.
- Installing SFTP/SSH Server
- Connecting to the server
Advertisement
- In Settings app, go to Apps > Apps & features > Manage optional features.
- Locate “OpenSSH server” feature, expand it, and select Install.
Binaries are installed to %WINDIR%System32OpenSSH. Configuration file (sshd_config) and host keys are installed to %ProgramData%ssh (only after the server is started for the first time).
You may still want to use the following manual installation if you want to install a newer version of OpenSSH than the one built into Windows 10.
- Download the latest OpenSSH for Windows binaries (package
OpenSSH-Win64.ziporOpenSSH-Win32.zip) - As the Administrator, extract the package to
C:Program FilesOpenSSH - As the Administrator, install sshd and ssh-agent services:
- Allow incoming connections to SSH server in Windows Firewall:
- When installed as an optional feature, the firewall rule “OpenSSH SSH Server (sshd)” should have been created automatically. If not, proceed to create and enable the rule as follows.
- Either run the following PowerShell command as the Administrator:
ReplaceC:System32OpenSSHsshd.exewith the actual path to thesshd.exe(C:Program FilesOpenSSHssh.exe, had you followed the manual installation instructions above). - or go to Control Panel > System and Security > Windows Defender Firewall1 > Advanced Settings > Inbound Rules and add a new rule for port 22.
- Start the service and/or configure automatic start:
- Go to Control Panel > System and Security > Administrative Tools and open Services. Locate OpenSSH SSH Server service.
- If you want the server to start automatically when your machine is started: Go to Action > Properties. In the Properties dialog, change Startup type to Automatic and confirm.
- Start the OpenSSH SSH Server service by clicking the Start the service.
These instructions are partially based on the official deployment instructions.
Follow a generic guide for Setting up SSH public key authentication in *nix OpenSSH server, with the following difference:
- Create the
.sshfolder (for theauthorized_keysfile) in your Windows account profile folder (typically inC:Usersusername.ssh).2 - For permissions to the
.sshfolder and theauthorized_keysfile, what matters are Windows ACL permissions, not simple *nix permissions. Set the ACL so that the respective Windows account is the owner of the folder and the file and is the only account that has a write access to them. The account that runs OpenSSH SSH Server service (typicallySYSTEMorsshd) needs to have read access to the file. - Though, with the default Win32-OpenSSH configuration there is an exception set in
sshd_configfor accounts inAdministratorsgroup. For these, the server uses a different location for the authorized keys file:%ALLUSERSPROFILE%sshadministrators_authorized_keys(i.e. typicallyC:ProgramDatasshadministrators_authorized_keys).
Before the first connection, find out the fingerprint of the server’s host key by using ssh-keygen.exe for each file.
In Windows command-prompt, use:
Replace %WINDIR%System32 with %ProgramFiles%, if appropriate.
In PowerShell, use:
Replace $env:WINDIRSystem32 with $env:ProgramFiles, if appropriate.
You will get an output like this:
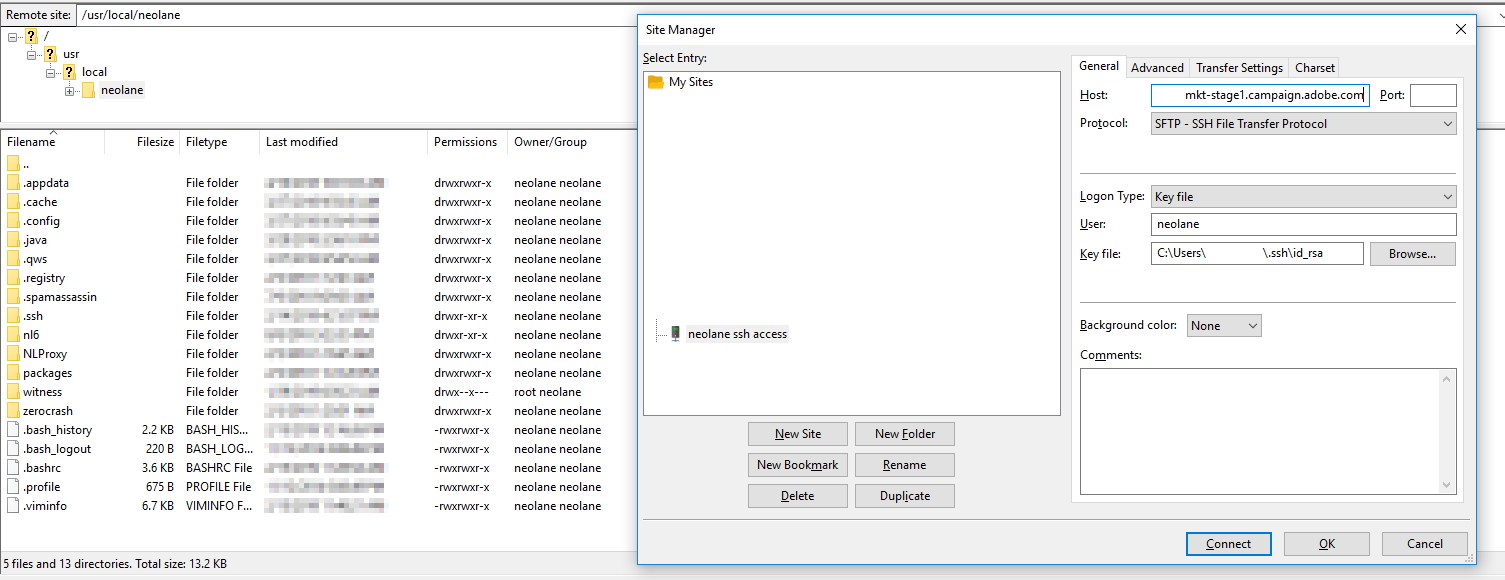
Start WinSCP. Login dialog will appear. On the dialog:
- Make sure New site node is selected.
- On New site node, make sure the SFTP protocol is selected.
- Enter your machine/server IP address (or a hostname) into the Host name box.
- Enter your Windows account name to the User name box. It might have to be entered in the format
user@domainif running on a domain. - For a public key authentication:
- Press the Advanced button to open Advanced site settings dialog and go to SSH > Authentication page.
- In Private key file box select your private key file.
- Submit Advanced site settings dialog with the OK button.
- For a password authentication:
- Enter your Windows account password to the Password box.
- If your Windows account does not have a password, you cannot authenticate with the password authentication (i.e. with an empty password), you need to use the public key authentication.
- Save your site settings using the Save button.
- Login using Login button.
- Verify the host key by comparing fingerprints with those collected before (see above).
Advertisement
If you cannot authenticate to the server and use Windows 10 Developer mode, make sure that your OpenSSH server does not conflict with an internal SSH server used by the Developer mode. You may need to turn off the SSH Server Broker and SSH Server Proxy Windows services. Or run your OpenSSH server on a different port than 22.
- Guide to Installing Secure FTP Server on Windows using IIS;
- Guide to uploading files to SFTP server;
- Guide to automating operations (including upload).
- Windows Firewall on older versions of Windows.Back
- Windows File Explorer does not allow you to create a folder starting with a dot directly. As a workaround, use
.ssh., the trailing dot will allow you to bypass the restriction, but will not be included in the name.Back
What is SFTP?
SFTP stands for SSH File Transfer Protocol. You guessed it correct. It is version of FTP that uses SSH on top. It allows users to upload and download files to and from a Linux server through an encrypted connection. FTP does the same without encryption and this is why SFTP is preferred over FTP these days.
Let’s see how you can set up a SFTP server on a Linux system.
Setting up SFTP Server on Linux
I have used Ubuntu in this tutorial. The installation commands are specific to Ubuntu and Debian but the rest of the steps can be followed in any other Linux distribution.
To perform the steps, you need have sudoer rights. So if you don’t sudo rights, contact your system administrator. If you are the one, please read about creating sudo user in Ubuntu.
Setting up SFTP is very easy. Before going to that, you need to have OpenSSH installed in the server side and SSH package in the client side.
I have discussed setting up SSH on Ubuntu in detail in a separate article, I’ll just mention the important steps here.
To install OpenSSH in server, you can use the following command:
You also need SSH on the system from where you are going to access the SFTP server.
After this is done, you will have everything ready to setup SFTP. It’s done in three steps and I am going to show it to you one-by-one.
Step 1: Create Groups, Users, Directories
To use SFTP (or any other service in general) safely, it is best to create groups and users to use that service and only that service. “It is best to give one specific right to one specific entity”.
In case if you want to give SFTP access and also normal system access, create users such that it is easy to identify them according to service. For example, if seeni is used for normal system access then seenisftp can be used for SFTP access. Using this method will be easier on the administration side.
Let’s create a group named “sftpg” using groupadd command:
Let’s create a user named “seenisftp” and add him to the above group and give him a password.
In the useradd command, -g option tells the group to which user should be added. You can list all the users in Linux and verify that the new user is has added.
Let’s assume you want to use the directory /data/ as your root for sftp and /data/USERNAME for each user. So when users login through sftp, they should be in /data/USERNAME as their default directory (Just like you are in /home/USERNAME directory when you login into the Linux system through SSH). Also, assume a constraint that they can read files from that directory but can upload only to uploadsdirectory.
Let’s create the directories and change their access and ownership as follows (read about file permissions in Linux to know more about it).
One thing that might confuse is giving ownership of the user’s directory to the root itself. This is mandatory for chrooting in SFTP. So make sure that owner of the /data/USERNAME is root.
As of now, we have user named seenisftp with group sftpg and with access permissions set for /data/seenisftp.
Step 2: Configure sshd_config
Next is you need to configure ssh server so that whenever user belonging to sftpg group logs in, he/she gets into sftp instead of the normal shell you get through ssh. Append the following snippet to /etc/ssh/sshd_config if not already present.
Match Group sftpg ChrootDirectory /data/%u ForceCommand internal-sftp

In the above snippet, ChrootDirectory allows the specified directory to be made as the root (“/” directory ) node in the directory tree. The logged in user cannot see anything above that directory. So it will stop the current user from accessing other user’s files through sftp. %u is the escape code for filling it with the current username at the time of login. When seenisftp logins through sftp, he will be in /data/seenisftp as his root directory. He will not be able to see anything above it.
Step 3: Restart the service
To make changes we made to sshd_config live, restart the service as follows.
Ssh Sftp Server
Accessing SFTP via Linux command line
You can login into SFTP as you normally would do with SSH.
Sample SFTP commands
SFTP commands are usually of the following format.
Sftp And Ssh Port
For any command, arguments may be either local system paths or remote system paths. There is no specific visible distinction between them. You can specify the path as normal after considering the whether the argument is local or remote.
GET – download contents from remote server to the local system. Below command downloads remote file poster.img to the local system’s ~/Pictures directory.
PUT – Upload contents form the local system to the remote system. Below command uploads the ~/Pictures/poster2.jpg into my uploads directory.
RM – To remove the files in the remote system. This is very similar to rm command. You can see that from below command which deletes an image at uploads/poster3.jpg
Above commands are very basic and are sufficient enough to explore the FTP/SFTP server. If you want to know more, either use help command or use this resource.

I hope this article helped you in setting up SFTP server on Linux.
Tell us in comments about what is your SFTP file system setup. Is it like mentioned in this article or a pooled directory or anything else?
If you found this article useful, share it with your friends. If you have suggestions, feel free to drop them below.
Become a Member for FREE
Enable Ssh Sftp Ubuntu
Join the conversation.
